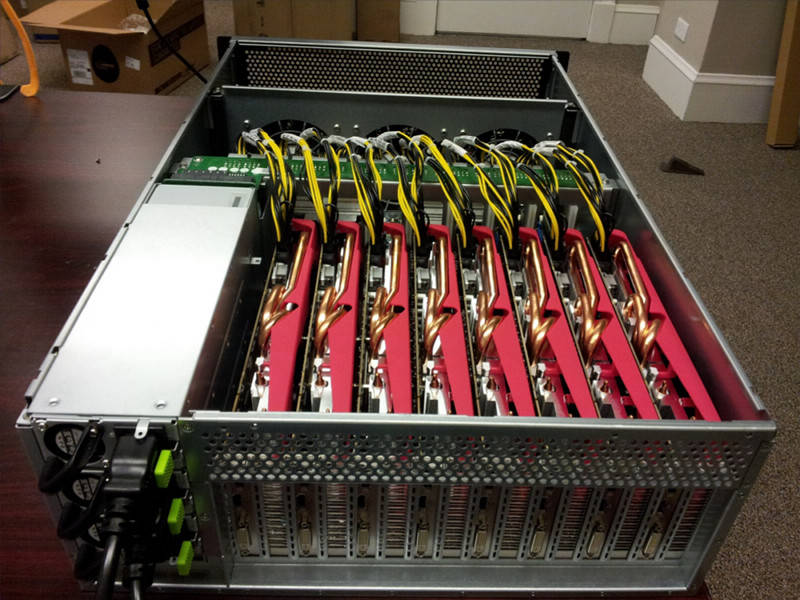
Security Ledger reports on a breakthrough in password-cracking, using 25 graphics cards in parallel to churn through astounding quantities of password possibilities in unheard-of timescales. It's the truly the end of the line for passwords protected by older hashing algorithms and illustrates neatly how yesterday's "password that would take millions of years to break" is this year's "password broken in an afternoon," and has profound implications for the sort of password hash-dumps we've seen in the past two years.
A presentation at the Passwords^12 Conference in Oslo, Norway (slides available here), has moved the goalposts, again. Speaking on Monday, researcher Jeremi Gosney (a.k.a epixoip) demonstrated a rig that leveraged the Open Computing Language (OpenCL) framework and a technology known as Virtual Open Cluster (VCL) to run the HashCat password cracking program across a cluster of five, 4U servers equipped with 25 AMD Radeon GPUs and communicating at 10 Gbps and 20 Gbps over Infiniband switched fabric.
Gosney's system elevates password cracking to the next level, and effectively renders even the strongest passwords protected with weaker encryption algorithms, like Microsoft's LM and NTLM, obsolete.
In a test, the researcher's system was able to churn through 348 billion NTLM password hashes per second. That renders even the most secure password vulnerable to compute-intensive brute force and wordlist (or dictionary) attacks. A 14 character Windows XP password hashed using NTLM (NT Lan Manager), for example, would fall in just six minutes, said Per Thorsheim, organizer of the Passwords^12 Conference.
New 25 GPU Monster Devours Passwords In Seconds [Security Ledger]
(via /.)





