To do in DC, Nov. 7: A digital security conference for journalists, bloggers
The event will focus on how news organizations and reporters can use technology and encryption to better protect their sources in the post-Snowden age.
The event will focus on how news organizations and reporters can use technology and encryption to better protect their sources in the post-Snowden age.
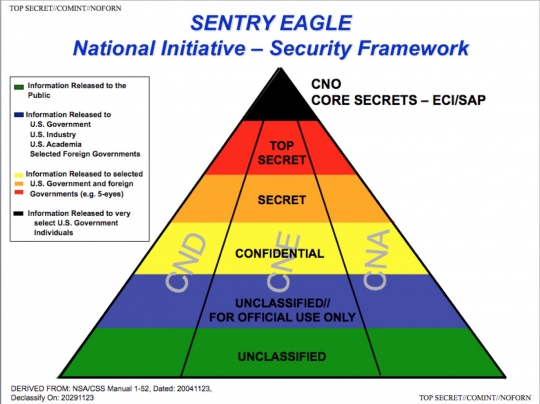
Leaked Snowden documents published by Laura Poitras and Peter Maass in The Intercept describe the NSA's SENTRY EAGLE program describe six programs aimed at weakening the capacity of people all over the world to communicate in private.
 Security failures will live on forever, because protocols have no sell-by date. Glenn Fleishman exposes the eternity we face with broken software.
Security failures will live on forever, because protocols have no sell-by date. Glenn Fleishman exposes the eternity we face with broken software.
 Glenn Fleishman on the tricky new user-tracking method that sees through privacy controls.
Glenn Fleishman on the tricky new user-tracking method that sees through privacy controls.

Yesterday at SXSW, Barton Gellman and I did a one-hour introductory Q&A before Edward Snowden's appearance. Right after Snowden and his colleagues from the ACLU wrapped up, I sat down and wrote up their event for The Guardian, who've just posted my impressions:

The ACLU and SXSW will host a video chat with Edward Snowden on Monday, during the day's civil-liberties-focused program track. I'll be speaking immediately before Snowden, with Barton Gellman, and we will be staying for the Snowden event. Snowden will be interviewed by ACLU technologist Christopher Soghoian, and the event is moderated by the ACLU's Ben Wizner. — Read the rest
New York's Attorney General, Eric Schneiderman, has subpoenaed AirBnB for user data on all active hosts in New York City "as part of an investigation into the website stemming from a 2010 law that makes it illegal to use such sites to rent out your own apartment," reports NYDN. — Read the rest

The Washington Post today published several big scoops related to the National Security Agency's surveillance programs. The paper's investigations were triggered by documents leaked to them "earlier this summer" by former NSA contractor Edward Snowden. He has sought political asylum from a number of nations, and is currently in Moscow. — Read the rest

Michael Morisy sez, "Back when the National Security Agency still measured data in megabytes rather than by the square mile of servers, the agency took it upon itself to catalogue the output of a newswire service and publications of the wider intelligence community, new documents show. — Read the rest
At Techdirt, Mike Masnick has further thoughts on the NYT piece on Prism, in which they try to resolve the contradiction between the NSA and Obama's admission that Prism exists and the leaked NSA slide deck is real, and the categorical (and eerily similar) denials from the companies involved (as well as Twitter's glaring absence from the list of cooperating companies):
— Read the restThis is not, by the way, the first time that we've seen Twitter stand up and fight for a user's rights against a government request for data.
Here's a must-read story from Tech Review about the thriving trade in "zero-day exploits" — critical software bugs that are sold off to military contractors to be integrated into offensive malware, rather than reported to the manufacturer for repair. The stuff built with zero-days — network appliances that can snoop on a whole country, even supposedly secure conversations; viruses that can hijack the camera and microphone on your phone or laptop; and more — are the modern equivalent of landmines and cluster bombs: antipersonnel weapons that end up in the hands of criminals, thugs and dictators who use them to figure out whom to arrest, torture, and murder. — Read the rest
Privacy International's 16-minute mini-documentary from DEFCON about privacy is a great, compact answer to the question, "Why does privacy matter?"

The Washington Post reports that the investigation into CIA chief David Petraeus began "when a woman whom he was having an affair with sent threatening e-mails to another woman close to him," citing "three senior law enforcement officials with knowledge of the episode" as sources. — Read the rest
A court filing from an FBI Special Agent reports that the Bureau's forensics teams can't crack the pattern-lock utility on Android devices' screens. This is moderately comforting, given the courts' recent findings that mobile phones can be searched without warrants. David Kravets writes on Wired:
— Read the restA San Diego federal judge days ago approved the warrant upon a request by FBI Special Agent Jonathan Cupina.
Twitter has bought a company called Whisper Systems, who make a secure version of the Android operating system as well as suites of privacy tools that are intended to protect demonstrators, especially participants in the Arab Spring. Many speculate that the acquisition was driven by the desire to hire CTO Moxie Marlinspike, a somewhat legendary cryptographer. — Read the rest
Sociologist danah boyd has posted her responses to a Wall Street Journal debate on privacy that included Stewart Baker, Jeff Jarvis, and Chris Soghoian. Boyd's responses are nuanced, evidence-based, and humane, and get well past the "privacy is dead" and "kids don't care about privacy, or they wouldn't be using Facebook" simplifications. — Read the rest

A U.S. company that makes Internet "filtering" systems admits that Syria has been using at least 13 of its devices to censor Web activity there. This news comes as the Syrian government cracks down on its citizens and silences their online activities. — Read the rest

The Wall Street Journal was the first to report tonight that Jacob Appelbaum, a hacker, security researcher, and human rights activist, is the subject of a secret court order demanding his email data for the last two years. Sonic.net, a small ISP, went to great trouble and expense to fight the order but lost. — Read the rest
Christopher Soghoian and Jake Appelbaum FOIA'd emails from BART related to the recent/ongoing Anonymous protests.
(Image contributed to the BB Flickr Pool by Bhautik Joshi)
Finally, here is BART's cop-out explanation for why they shut down wireless service in Bay Area stations on Aug. 11.
— Read the restBART temporarily interrupted service at select BART stations as one of many tactics to ensure the safety of everyone on the platform.