
Brian Krebs writes about how hackers have expanded the ways they extract value from compromised PCs. No longer is a compromised machine merely good for forming part of a botnet or forwarding spam. New strains of malware extract all your login/passwords for ecommerce sites, and these are then put on sale at $2 a throw on sites like Freshtools. — Read the rest
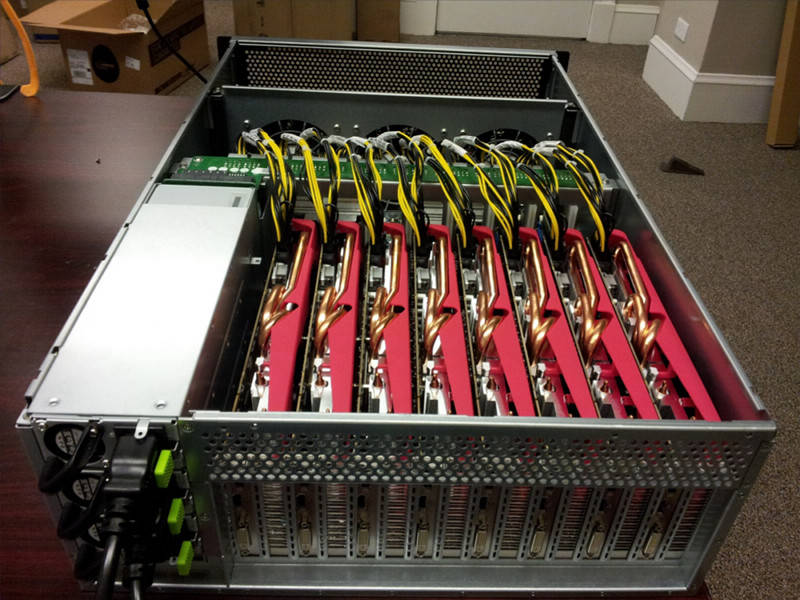
Security Ledger reports on a breakthrough in password-cracking, using 25 graphics cards in parallel to churn through astounding quantities of password possibilities in unheard-of timescales. It's the truly the end of the line for passwords protected by older hashing algorithms and illustrates neatly how yesterday's "password that would take millions of years to break" is this year's "password broken in an afternoon," and has profound implications for the sort of password hash-dumps we've seen in the past two years. — Read the rest
"Superb fairy-wren (Malurus cyaneus) mothers sing to their unhatched eggs to teach the embryo inside a 'password' — a single unique note — which the nestlings must later incorporate into their begging calls if they want to get fed." Zoë Corbyn in Scientific American, on a very unusual example of avian communication.
An update on the Twitter Status blog explains that the service "unintentionally reset passwords of a larger number of accounts, beyond those… believed to have been compromised." Twitter wasn't hacked, it just goofed and accidentally sent re-set instructions to too many users.
The FTC has settled with seven rent-to-own companies and a software company called DesignerWare of North East Pennsylvania for their role in secretly installing spyware on rental laptops, which was used to take "pictures of children, individuals not fully clothed, and couples engaged in sexual activities." — Read the rest
The dump of 450,000 Yahoo passwords by a group calling itself "D33ds Company" has been analyzed by Anders Nilsson (apparently these passwords were stored in the clear). Here's the topline:
Total entries = 442773
Total unique entries = 342478
Top 10 passwords
123456 = 1666 (0.38%)
password = 780 (0.18%)
welcome = 436 (0.1%)
ninja = 333 (0.08%)
abc123 = 250 (0.06%)
123456789 = 222 (0.05%)
12345678 = 208 (0.05%)
sunshine = 205 (0.05%)
princess = 202 (0.05%)
qwerty = 172 (0.04%)
Top 10 base words
password = 1373 (0.31%)
welcome = 534 (0.12%)
qwerty = 464 (0.1%)
monkey = 430 (0.1%)
jesus = 429 (0.1%)
love = 421 (0.1%)
money = 407 (0.09%)
freedom = 385 (0.09%)
ninja = 380 (0.09%)
writer = 367 (0.08%)
Password length (length ordered)
1 = 117 (0.03%)
2 = 70 (0.02%)
3 = 302 (0.07%)
4 = 2748 (0.62%)
5 = 5323 (1.2%)
6 = 79610 (17.98%)
7 = 65598 (14.82%)
8 = 119125 (26.9%)
9 = 65955 (14.9%)
10 = 54756 (12.37%)
11 = 21219 (4.79%)
12 = 21728 (4.91%)
Statistics of the "450.000 leaked Yahoo accounts". — Read the rest
In the wake of a series of very high-profile password leaks, Brian Krebs talks to security researcher Thomas H. Ptacek about the best practices for securing passwords. The trick isn't to merely hash with a good salt — you must use a slow password hash that takes a lot of work, so that making rainbow tables is impractical. — Read the rest
As you've no doubt heard, a large tranche of hashed LinkedIn passwords has been leaked onto the net. There's no known way to turn the hash of a password back into the password itself, but you can make guesses about passwords, hash the guesses, and see if the hashed guess matches anything in the leaked database. — Read the rest

Elinor Mills at CNET digs into who leaked thousands of username/email/password sets yesterday, and what Twitter is doing about it.
Here are the Pastebin leaks, in case you want to check to see if your account was one of the ones published: one, two, three, four, five. — Read the rest
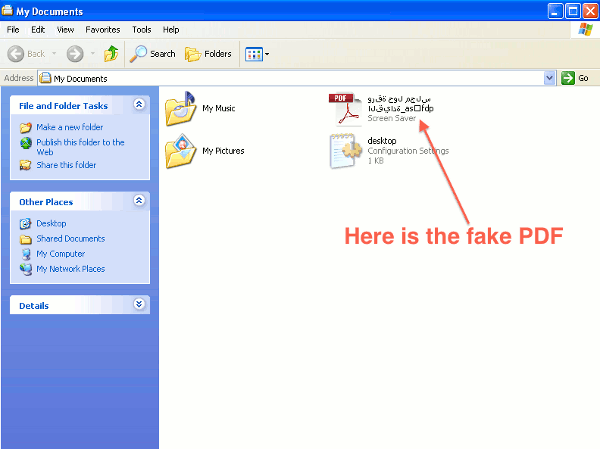
A fake PDF purporting to contain information on "the formation of the leadership council of the Syrian revolution" is circulating. As the Electronic Frontier Foundation's Eva Galperin and Morgan Marquis-Boire report, it's bad news for people who install it.
The latest surveillance malware comes in the form of an extracting file which is made to look like a PDF if you have file extensions turned off.
— Read the rest
US senators are calling for action on employers' habit of demanding employees' Facebook passwords, but no one seems to notice that many companies configure their computers so that they can eavesdrop on your Facebook, bank, and webmail passwords, even when those passwords are "protected" by SSL. — Read the rest
In "Linguistic properties of multi-word passphrases" (PDF, generates an SSL error) Cambridge's Joseph Bonneau and Ekaterina Shutova demonstrate that multi-word passphrases are more secure (have more entropy) than average user passwords composed of "random" characters, but that neither is very secure. — Read the rest

Matt Richtel's recent NYT article on teenagers who share their Facebook passwords as a show of affection has raised alarms with parents and educators who worry about the potential for bullying and abuse.
But as danah boyd points out the practice of password-sharing didn't start with kids: it started with parents, who required their kids to share their passwords with them. — Read the rest
SplashData, a company that makes password management tools, has released a roundup of 2011's "25 worst passwords," gleaned from password-dumps posted by "hackers" (presumably, sources like the Lulzsec Sony password files). I can't locate the actual study and its methodology (are these passwords "worst" because they're the most common, or because they contain the least entropy? — Read the rest
Microsoft's free email service, Hotmail, is forbidding the use of particularly awful passwords. In a story at Ars Technica, Peter Bright describes how it's taking measures to prevent users compromising themselves.
Anyone creating a new Hotmail account or changing the password of an existing account won't be able to use obvious and common passwords like "123456" or "password."
— Read the rest
The Agile Bits blog discusses good methods for choosing a human-memorable "master password" that is used to lock up a file of non-memorable, strong passwords:

Avoid secrets or things that are personally meaningful
The more personally meaningful something is to you the fewer alternatives there are.
— Read the rest
While it's pretty awful that a million Sony users' passwords and 0.25 million Gawker passwords were published online, it has made for an interesting comparative analysis of the weaknesses in password protection, a subject near and dear to many security researchers' hearts. — Read the rest
45-year-old Terry Childs, a former sysadmin for the city of San Francisco, was sentenced Friday to four years in prison for refusing to hand over administrative passwords to the city's FiberWAN network back in July 2008. A judge convicted Childs in April of violating state hacking laws. — Read the rest

WPA Cracker is a WiFi security compromiser in the cloud, running on a high-performance cluster. Send them a dump of captured network traffic and $35, and they will try 136 million passwords in 40 minutes, tops (for $17, they'll run the same attack at half speed) — the same crack would take five days on a "contemporary desktop PC." — Read the rest

[Link via Laughing Squid]







