The New Yorker today launched 'Strongbox,' a whistleblower submission system designed to allow anonymous leakers to digitally transmit important information to journalists.
"The underlying code, called 'Dead-Drop,' is an open-source project and was written by the Internet pioneer and legendary coder Aaron Swartz, before he tragically died in January," writes Trevor Timm at a Freedom of the Press Foundation blog post.
"You can read the underlying code here and the details for how it works and the background, written by the project's manager Kevin Poulsen, here."
Strongbox makes use of the anonymizing Tor network.
From the introductory newyorker.com blog post by Amy Davidson:
Strongbox is a simple thing in its conception: in one sense, it's just an extension of the mailing address we printed in small type on the inside cover of the first issue of the magazine, in 1925, later joined by a phone number (in 1928—it was BRyant 6300) and e-mail address (in 1998). Readers and sources have long sent documents to the magazine and its reporters, from letters of complaint to classified papers. (Joshua Rothman has written about that history and the magazine's record of investigative journalism.) But, over the years, it's also become easier to trace the senders, even when they don't want to be found. Strongbox addresses that; as it's set up, even we won't be able to figure out where files sent to us come from. If anyone asks us, we won't be able to tell them.
The project was many months in the making, but launches at an interesting time: just days after the Associated Press revealed the Justice Department had secretly acquired some 60 days of call records for 20 different AP phone lines, in a leak investigation involving the outing of a CIA agent in Saudi Arabia.
Projects like this need deep security scrutiny from the security community. Now that it's launched, of course, that can happen more easily; the open-source nature of the project could help facilitate robust review.
This won't be the first time that a news organization has launched a Wikileaks-style leak transmission system—Al-Jazeera and the WSJ encountered big problems when they launched similar projects two years ago, and their usefulness is dubious. Hopefully Strongbox won't suffer the same fate.
Again, Trevor Timm at Freedom of the Press Foundation (disclosure: I'm a board member):
Leaks have never been more critical to democracy, given that government secrecy is at an all time high. Countless times over past decade—from NSA warrantless wiretapping and CIA secret prisons, to secret drone strikes and unprecedented cyberattacks—leaks have exposed corruption, wrongdoing, and illegality in government when the flow of information has been stifled through other channels. In fact, virtually every unconstitutional action by the government over the last decade was initially uncovered by a leak to the press.
Yet when WikiLeaks was operating a submission system three years ago and published secret government information in the public interest, they were attacked by government officials, pundits, and sometimes even journalists. This, despite the fact, their actions were protected by the First Amendment, just like when the New York Times or Washington Post receives classified information from a government source in the physical world.
Hopefully this project will remind people that these types of WikiLeaks-like submission systems should proliferate, not wither away.
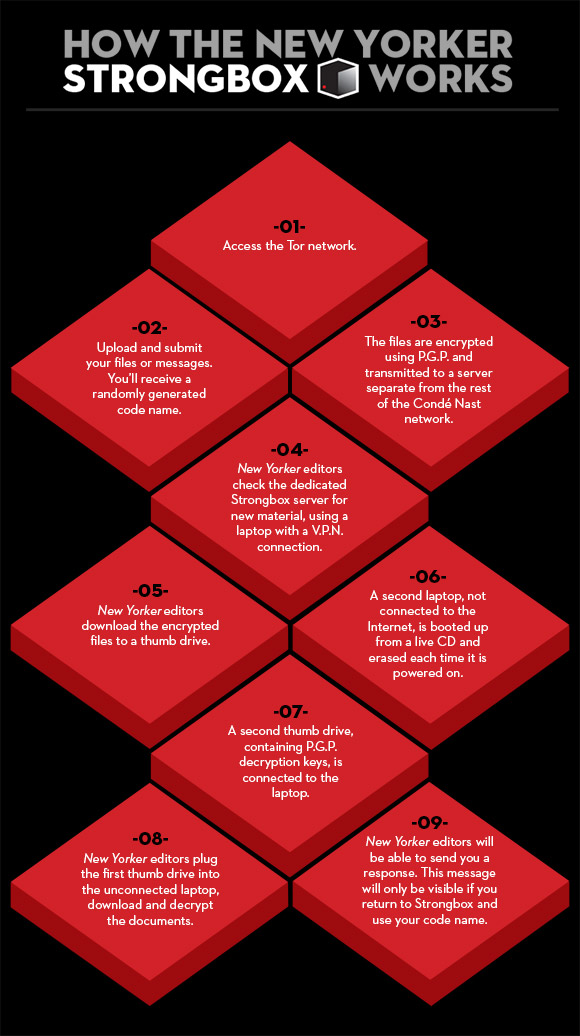
A New Yorker graphic maps out how Strongbox is designed to work: "Multiple computers, thumb drives, encryption, and Tor are all involved."
(via Trevor Timm)